Endpoint Detection and Response (EDR)
Overview:
The EDR Module helps protect your environment by continuously monitoring endpoints for suspicious activity and malware. It provides real-time detection, endpoint isolation, and detailed event tracking to ensure your devices remain secure and compliant.
Key Features:
- Endpoint Detection & Response: Real-time threat detection with endpoint isolation capabilities.
-
Managed Endpoint Monitoring: Track online, offline, and unhealthy endpoints.
-
Authentication Tracking: Monitor successful and failed authentication attempts.
-
Event Logging: Detailed event activity logs to analyze endpoint behavior.
-
Recurring Offender Identification: Detect repeated threats for proactive response.
Pre-requisites
- Access to CyTech - AQUILA
-
Only users assigned the "Owner" or "Admin" role can access the Control Panel page within this module.
-
Step 3: Choose Endpoint Detection and Response (EDR).
Step 4: Hover into leftmost panel to view all the CSPM sections. This Process is applicable in all navigating into a Module.
Dashboard
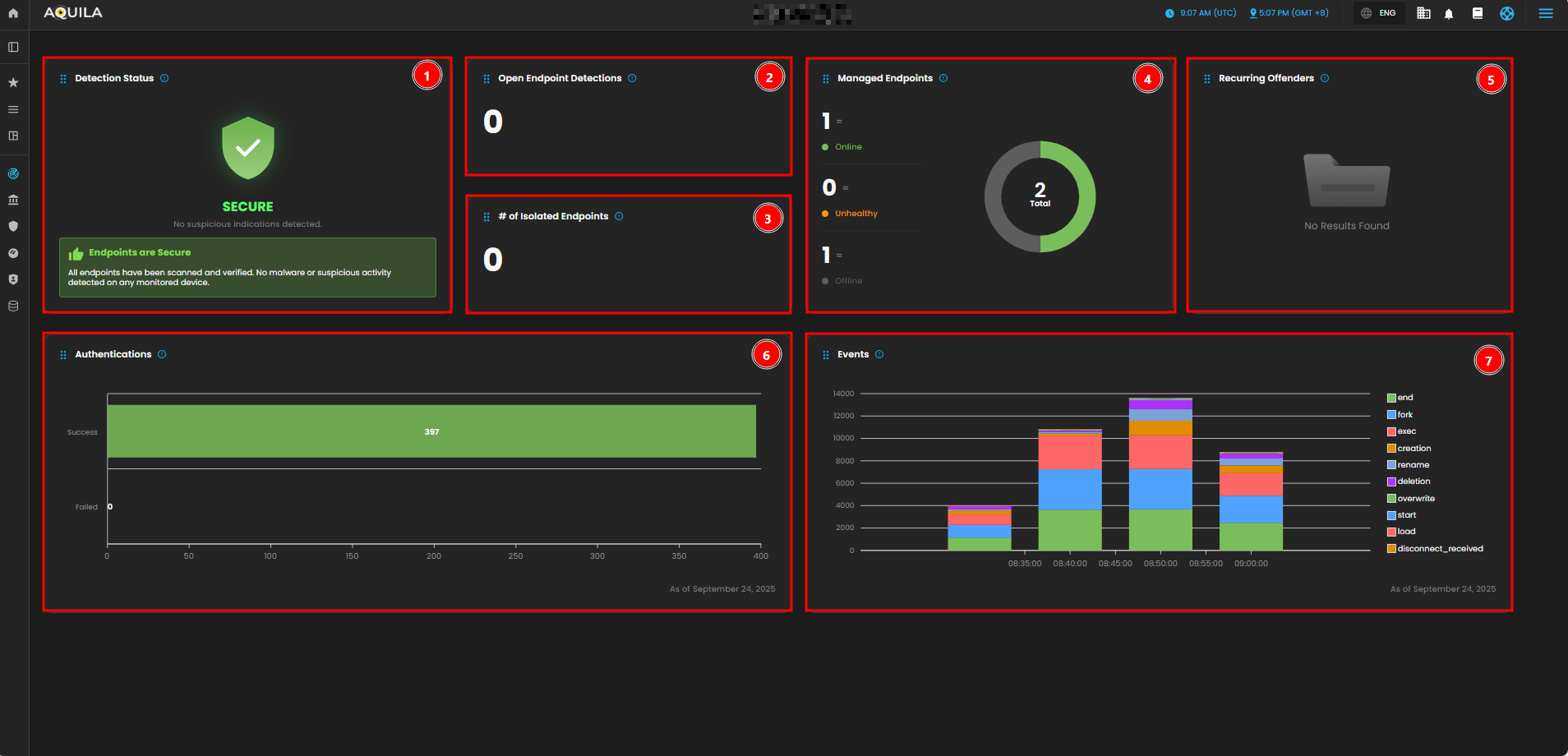
In the EDR Module Dashboard, you can monitor the security status of your endpoints at a glance. This includes Detection Status, Endpoint Health, Authentication Attempts, Event Activity, and Recurring Offenders.
-
Detection Status:
-
This widget shows the overall security status of the monitored endpoints. It indicates that there are no suspicious activities or malware detected. The green "SECURE" status confirms that the system is not facing any security issues at the moment.
-
-
Open Endpoint Detections:
-
Displays the number of currently active endpoint detections. This number is currently 0, meaning there are no open or unresolved detections.
-
-
Number of Isolated Endpoints:
-
Displays the number of endpoints that have been isolated due to detected threats or suspicious activities. The value is 0, indicating that no endpoints have been isolated.
-
-
Managed Endpoints:
-
Shows a breakdown of the endpoints under management. There is one endpoint marked as "Online" (green), and one is "Offline" (gray). The "Unhealthy" count is 0, which suggests no issues with endpoint health.
-
-
Recurring Offenders:
-
This widget lists any repeated offenders or recurring threats detected across the endpoints. It shows "No Results Found," meaning there are no repeated malicious activities detected at the moment.
-
-
Authentication:
-
Provides a graph showing the number of successful versus failed authentications. As of the latest data, there have been 397 successful authentications and 0 failed attempts, suggesting no authentication issues.
-
-
Events:
-
Displays the graphical representation of various system events over time. The chart breaks down different types of events (e.g., "end", "fork", "exec", etc.) that occurred between 08:35 and 09:00. The graph shows how these events fluctuate over time, with certain actions peaking during specific periods.
-
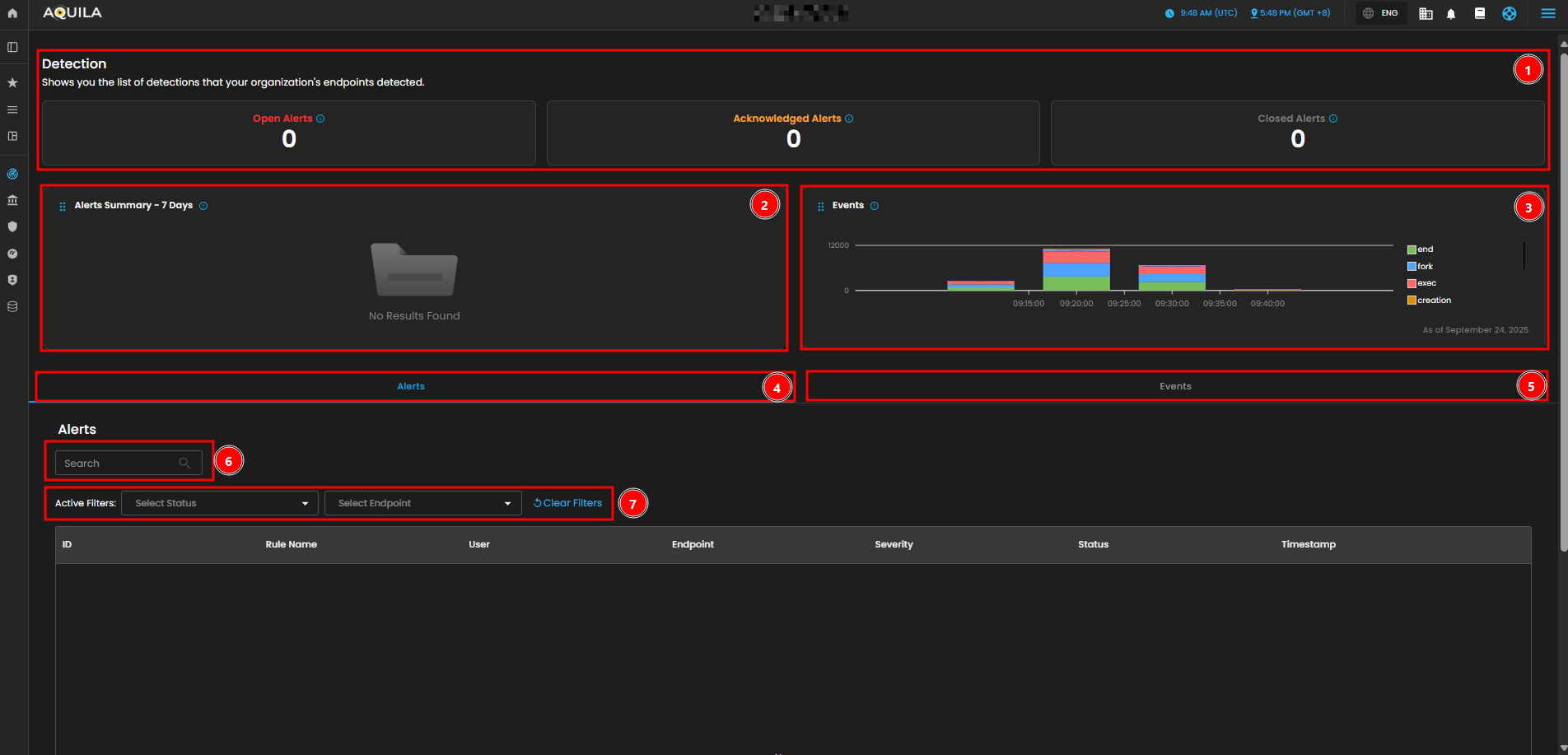
Detections
In the Detections,Detections, you can manage and analyze all detection and alert data. It includes an overview of open, closed, and acknowledged alerts, event activity trends, and detailed alerts with filtering capabilities.
-
Detections
-
Open Alerts and Acknowledged Alerts give you a quick overview of the current alerts that are either unresolved or acknowledged by users. As of now, there are no open or acknowledged alerts.
-
- Alert Summary
-
The Alerts Summary - 7 Days section shows a historical overview of detections from the past week. At the moment, it shows no results, indicating no major alerts have been triggered recently.
-
- Events Graph
-
The Events graph visualizes system activity, with each color representing different types of events like “end,” “fork,” “exec,” and “creation.” This graph provides insights into endpoint activity over time, showing fluctuations between 09:00 and 09:45 AM. For example, we can see spikes in events at certain times, allowing you to quickly identify periods of increased activity.
-
- Alerts Tab
-
The Alerts section allows you to search for specific alerts using the search bar. This feature helps you quickly locate an alert by its ID, user, or rule name.
-
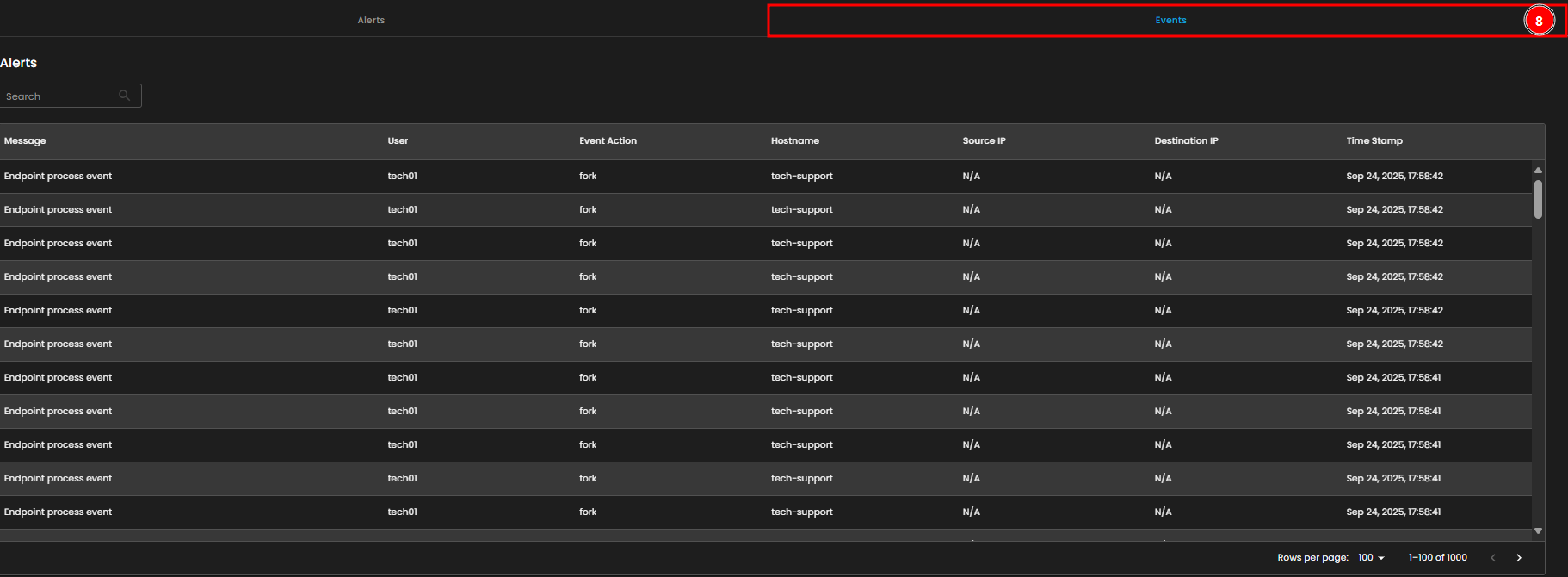
- Events Tab
-
The Events tab contains detailed logs of endpoint process events, including the user, event action, hostname, source and destination IPs, and timestamps. This tab enables you to investigate and track specific activities and behaviors occurring on
yourendpoints.
-
- Activity Filter
- The Active Filters allow you to filter the alerts by status (e.g., open, acknowledged, or closed) and endpoint. You can clear any applied filters with the “Clear Filters” button.
- Alerts Table
-
The Alerts Table shows detailed information for each alert, such as ID, rule name, user, endpoint, severity, status, and timestamp. Currently, there are no alerts listed, but this section would display them if there were any.
-
- Events Table
- The Events Table below provides a detailed list of endpoint process events, including information such as the user who triggered the event, the event action, the hostname, source and destination IPs, and timestamps. This helps in tracing specific activities happening on endpoints.
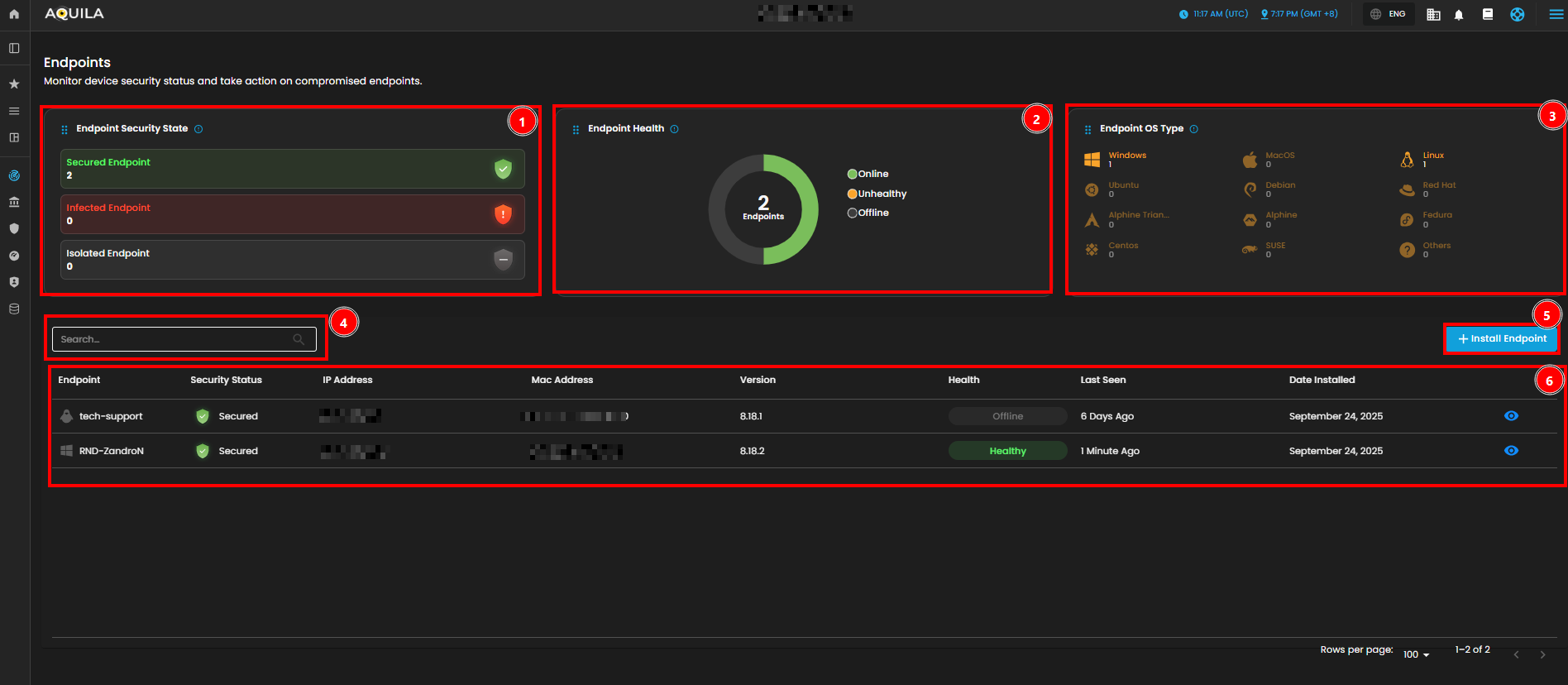
Endpoints
In the Endpoints Page, you can view a general summary of organization’s endpoint security status. This includes metrics such as secured, infected, and isolated endpoints. As of now, there are no infected or isolated endpoints in the system.
- Endpoint Security State
- This section provides a summary of the security state of endpoints. It displays the count of endpoints that are secured, infected, and isolated. At the moment, there are 2 secured endpoints, with no infected or isolated endpoints.
- Endpoint Health Overview
- The Endpoint Health section gives a snapshot of the health status of organization’s endpoints. It shows whether an endpoint is healthy, unhealthy, or offline. Currently, 2 endpoints are listed, with 1 healthy and 1 offline.
- Endpoint OS Type Distribution
- This section breaks down the operating system types of the endpoints across the network. It helps identify the diversity of operating systems in organization. For instance, 1 endpoint is running Windows, and another is using Linux.
- Endpoint List
- The Endpoint List section shows detailed information about each endpoint within a network. This includes the endpoint name, security status, IP address, MAC address, version, health status, and when it was last seen. At the moment, there are no alerts for compromised or unhealthy endpoints.
- Search Bar
- The Search Bar provides an easy way to quickly search for a specific endpoint by its name, IP address, security status, or health. This helps streamline navigation, especially when dealing with a large number of endpoints.
- Install Endpoint
- To add new endpoints to the system, click the Install Endpoint button. This will start the process of onboarding new devices into a network, allowing them to be tracked and secured like the existing endpoints.
Control Panel
In the Control Panel, you can manage various security settings and configurations for your organization’s endpoints. This section gives you access to several tools for managing Policies, Manage Endpoints, Trusted Applications, Event Filters, Host Isolation Exception and Blocklist. The control panel helps streamline the process of securing and monitoring endpoints, providing easy access to the most critical settings.
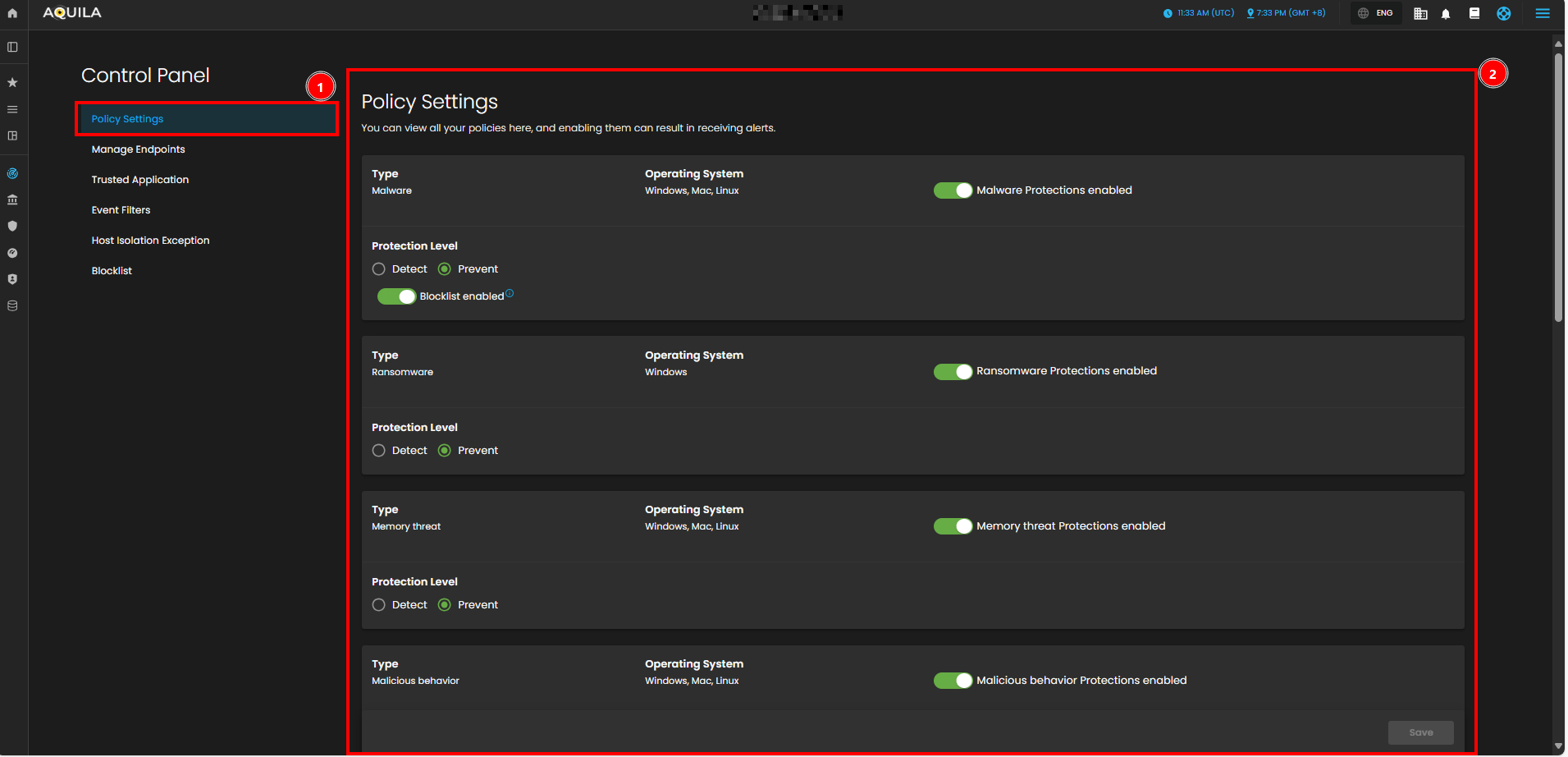
Policy Settings
In the Policy Settings Page, you can view and manage organization’s security policies. This includes configuring protection levels for various types of threats, such as malware, ransomware, memory threats, and malicious behavior. Currently, all protection policies are enabled with options to either detect or prevent these security risks across supported operating systems (Windows, Mac, Linux).
- Policy Settings Overview
- In the Policy Settings section, you can manage and view all the security policies set for your organization's endpoints. This section allows you to control and configure various protection levels for different types of security threats. Policies can be applied to endpoints based on their operating system (Windows, Mac, Linux), and enabling these policies can trigger alerts for the respective security events.
- Policy Settings Panel
- The Policy Settings Panel displays the different types of protection policies in place for your endpoints. Each policy corresponds to a specific security threat, such as malware, ransomware, memory threats, or malicious behavior. You can configure the protection level for each policy by toggling between Detect and Prevent options. Additionally, a blocklist feature can be enabled or disabled to provide further protection against unwanted software or threats.
-
-
-
Malware Protection: Enabled with options to Detect or Prevent.
-
Ransomware Protection: Enabled for Windows endpoints with Detect or Prevent options.
-
Memory Threat Protection: Enabled for all operating systems (Windows, Mac, Linux) with Detect or Prevent options.
-
Malicious Behavior Protection: Enabled for all operating systems (Windows, Mac, Linux) with the same detection or prevention options.
-
-
- Each policy has a toggle switch to enable or disable protection for the corresponding threat, and these settings can be easily modified according to your needs.
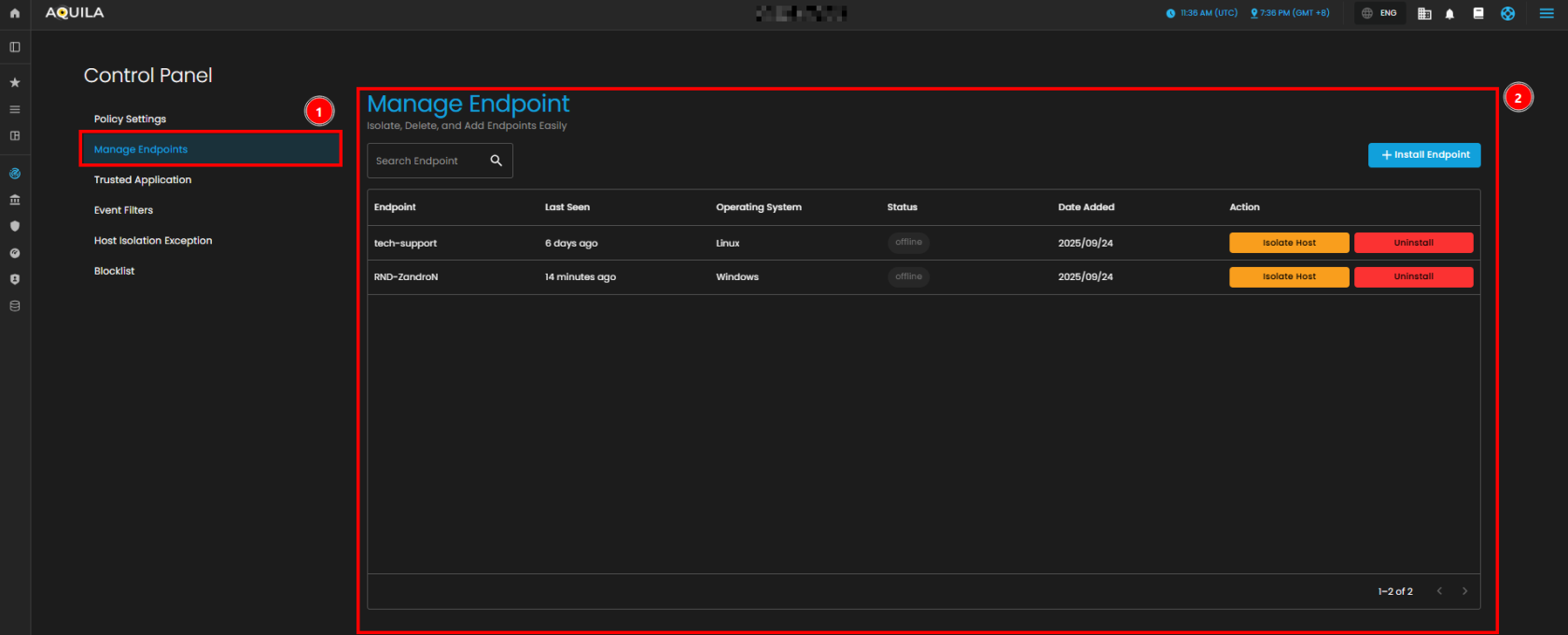
Manage Endpoints
In the Manage Endpoints Page, you can easily isolate, delete, or add new endpoints to your system. This section provides a quick overview of all your endpoints, including details like the endpoint name, last seen time, operating system, and status. Currently, all protection policies are enabled with options to either detect or prevent security risks across the endpoints in your system.
- Manage Endpoints Overview
- In the Manage Endpoints Page, you can easily isolate, delete, or add new endpoints to your system. This section provides a quick overview of all your endpoints, including details like the endpoint name, last seen time, operating system, and status.
- Endpoint List and Actions
- This section displays a list of all endpoints currently in your network. Each endpoint entry shows the following details:
- Endpoint Name: Identifies the device in the system.
- Last Seen: Indicates when the endpoint was last connected to the network.
- Operating System: Displays the OS of the endpoint (e.g., Linux, Windows).
- Status: Shows whether the endpoint is currently online or offline.
- Each endpoint can be acted upon with available options, such as isolating the host (for security reasons) or uninstalling it from the system. Currently, all endpoints listed are marked as offline.
- This section displays a list of all endpoints currently in your network. Each endpoint entry shows the following details:
- Search Endpoint
- The Search Endpoint bar at the top allows you to quickly locate specific endpoints in your system by searching for their names or other attributes.
- Install Endpoint
- To add new endpoints to your network, click the Install Endpoint button. This will allow you to initiate the process of registering new devices to be tracked and managed within your system.
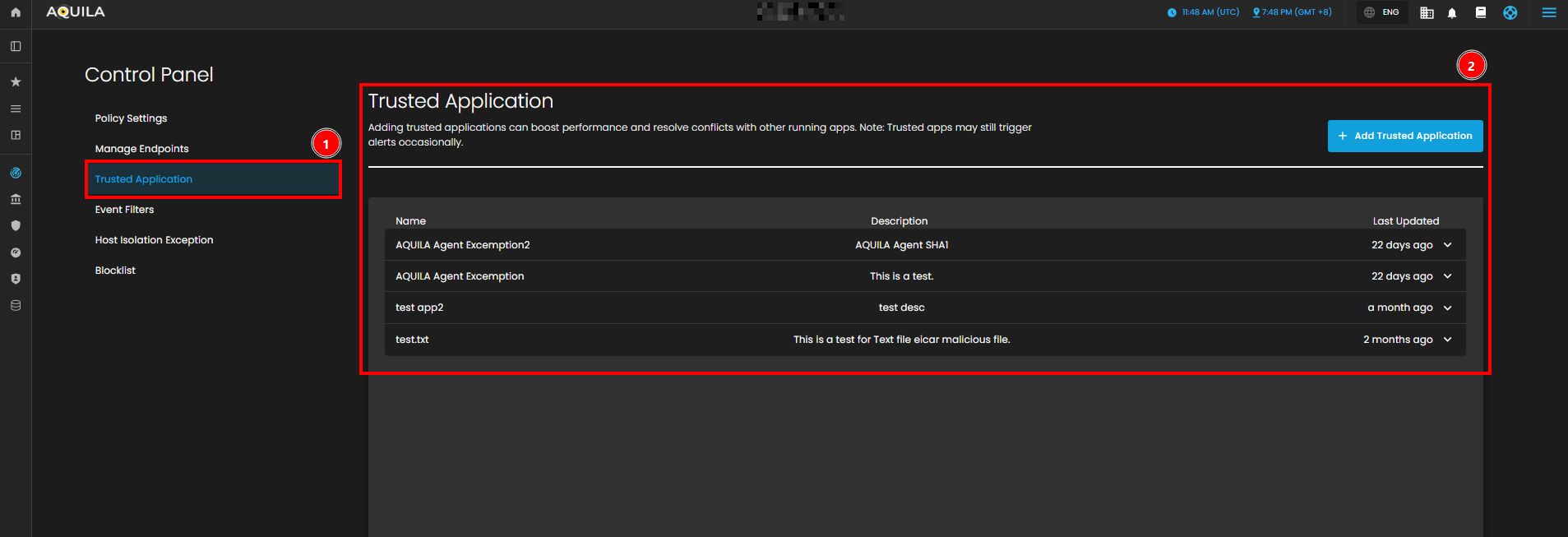
Trusted Application Page
In the Trusted Application Page, you can see an overview of your organization's trusted applications. This section includes the names of the applications, their descriptions, and the last updated time. Currently, there are several trusted applications listed, such as "AQUILA Agent Exception" and "test app2."
- The Trusted Application Overview
- This provides a list of the currently trusted applications along with their descriptions and the most recent updates. These applications are categorized by the name of the application and a brief description of their purpose.
- The Application Details Table
- It displays additional details, including the application name, description, and the timestamp of the last update. This table helps you track which applications are trusted and their associated descriptions. You can also update or remove any trusted application from this section.
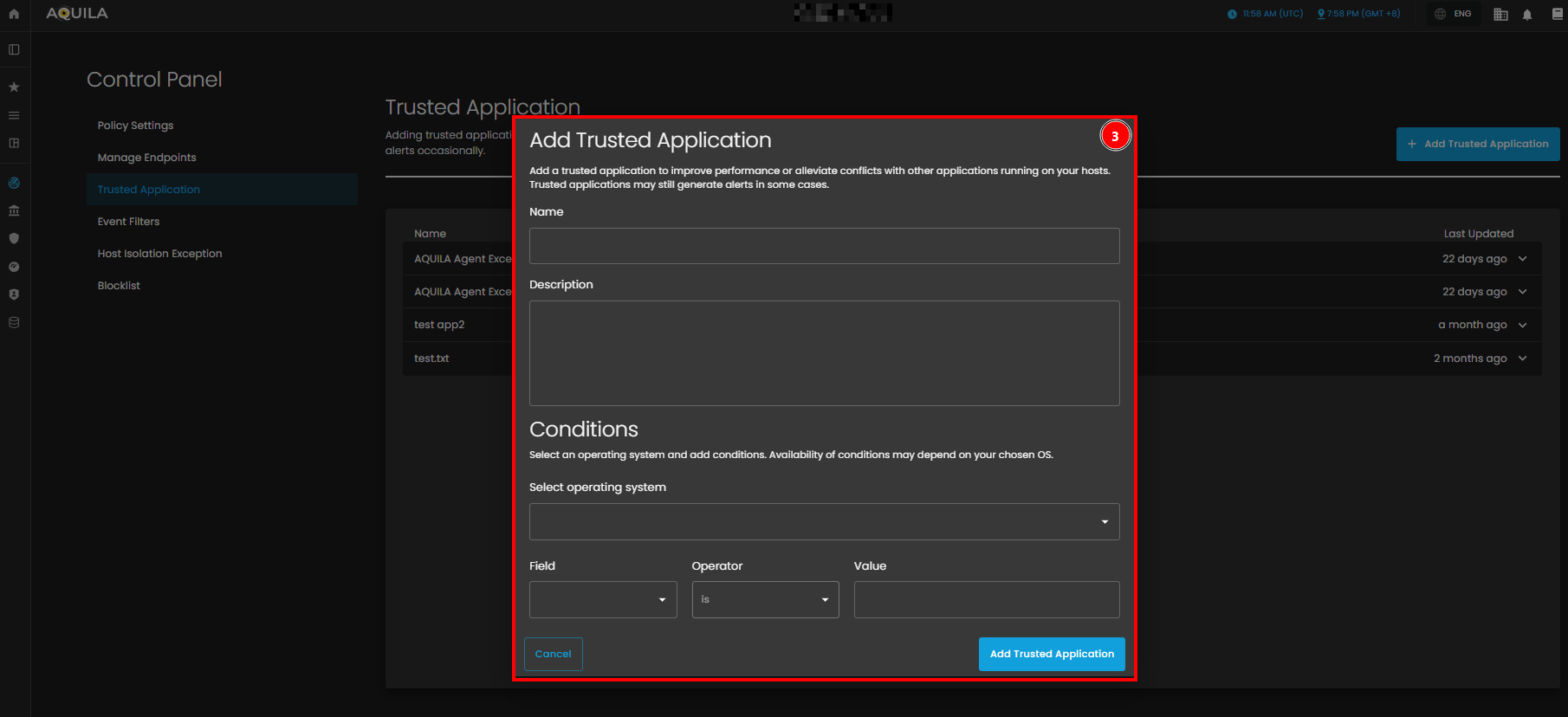
- Add Trusted Application
- This popup allows users to input the Name and Description of the trusted application. Additionally, it includes a Conditions section where you can select an operating system and specify conditions using fields, operators, and values. At the bottom, there are two buttons: Add Trusted Application to confirm the addition, and Cancel to discard the action.
Event Filters Page
In the Event Filters Page, you can assign or manage event filters that define which events should be tracked for your endpoints. Currently, there are no event filters assigned to any of the endpoints, as the section shows the message "No Assigned Event Filters."
- Event Filters
- The Assign Events Filters Option allows you to easily configure and apply filters to events, helping you focus on specific types of activities or behaviors across your endpoints. This will enable you to narrow down the event logs to show only relevant information.
- The Empty Event Filter Status
- It shows that no filters have been assigned yet, but it provides a clear call-to-action to add event filters.
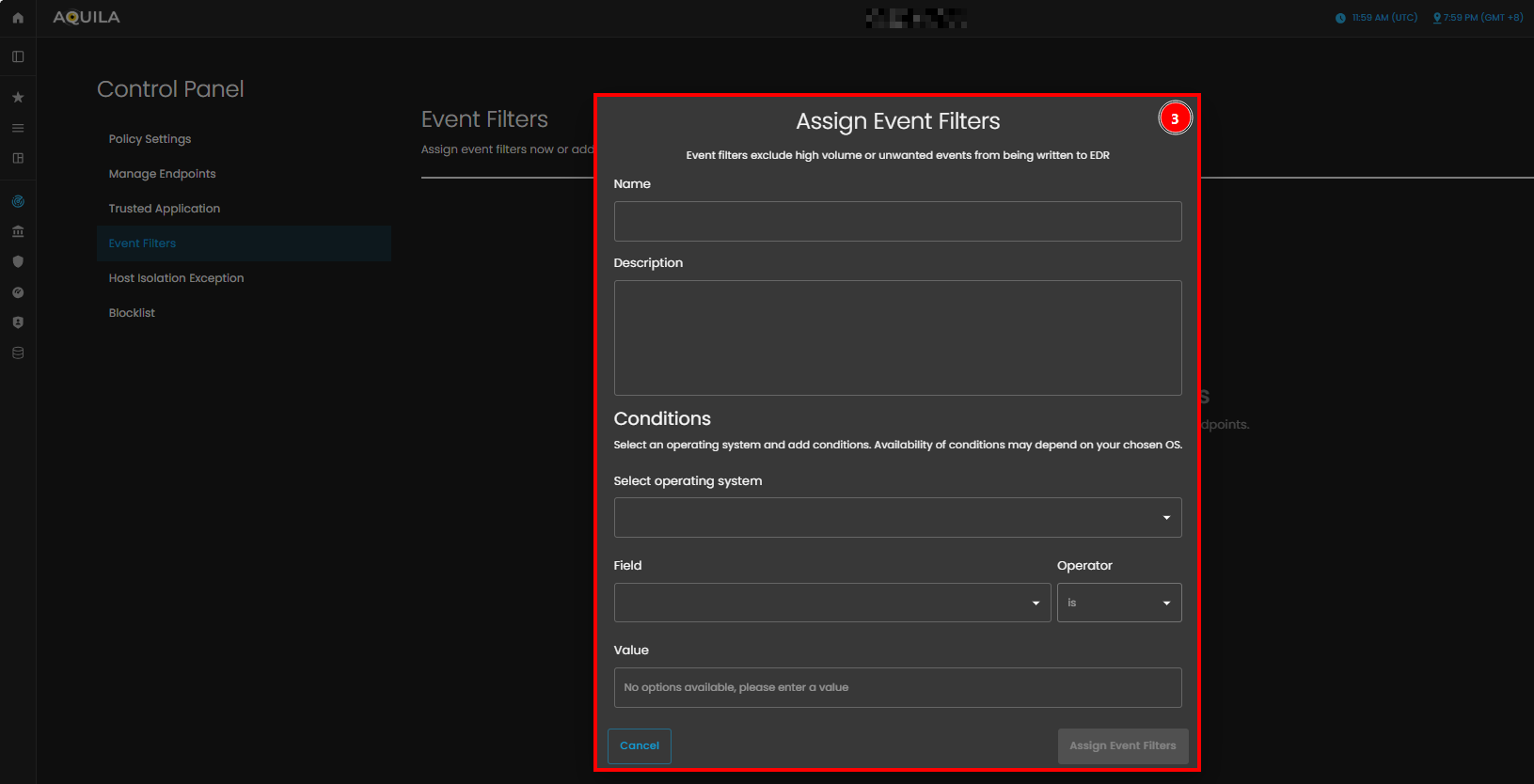
- Assign Event Filters
- This section allows users to configure filters that exclude high volume or unwanted events from being written to the EDR (Endpoint Detection and Response) system. It includes fields for the Name and Description of the event filter, both of which can be filled out with relevant details. Below that, the Conditions section lets you select an operating system and apply specific conditions using Field, Operator, and Value to filter events based on certain criteria.
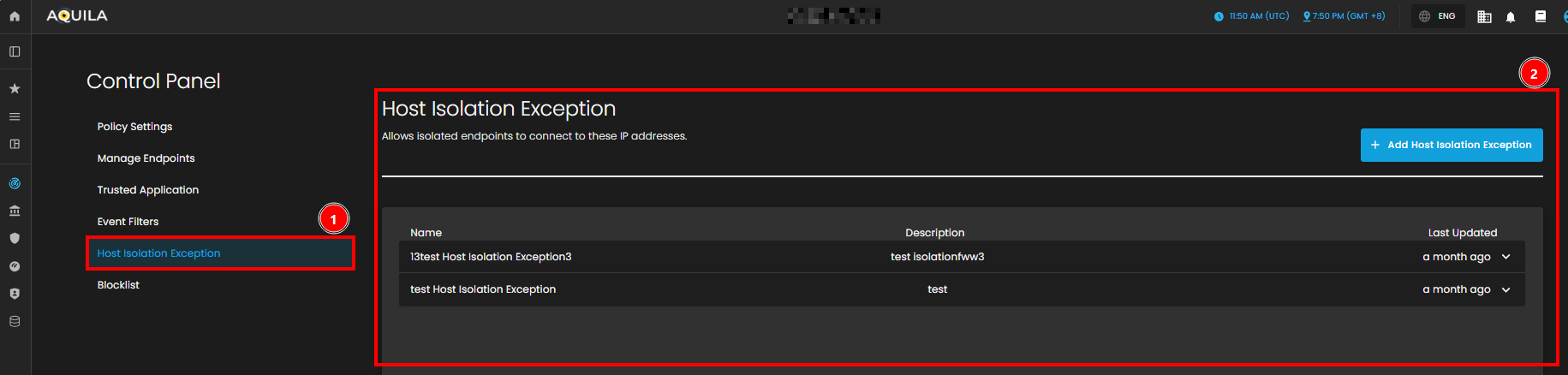
Host Isolation Exception Page
In the Host Isolation Exception Page, you can see the list of exceptions that allow isolated endpoints to connect to specific IP addresses. This section displays the names of the exceptions, their descriptions, and the most recent update times.
- The Host Isolation Exception Overview
- This gives you the ability to manage exceptions made to the host isolation policy. Here, you can track any exceptions, such as "test Host Isolation Exception," that have been made to allow endpoints to access certain IPs.
- The Exception Details Table
- It lists the exception names, descriptions, and the timestamp of when they were last updated. You can use this table to manage and modify these exceptions, ensuring proper access while maintaining security policies.
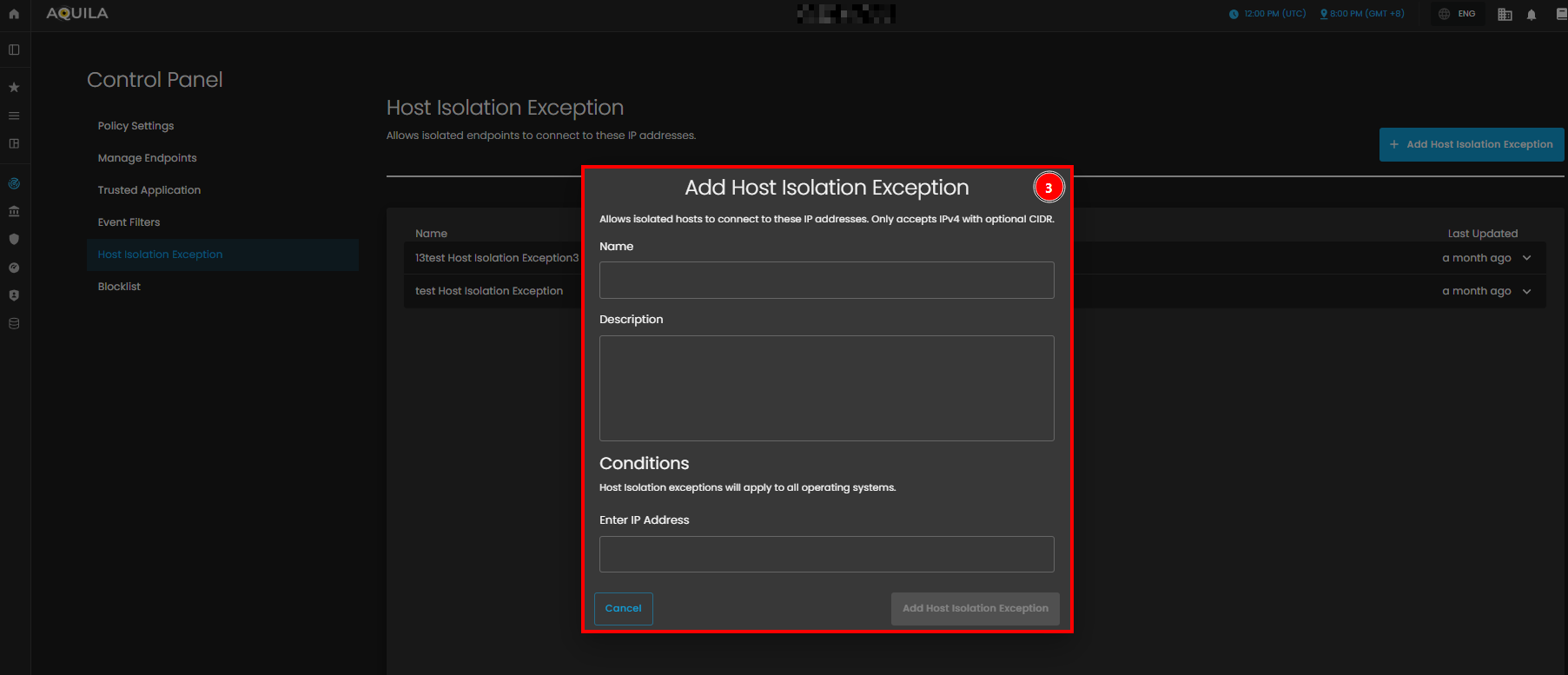
- Add Host Isolation Exception.
- This popup allows users to create exceptions for isolated hosts, enabling them to connect to specific IP addresses. It includes fields for the Name of the exception and an optional Description to provide additional details. Under Conditions, there is a field labeled Enter IP Address, where users can specify the IP addresses (IPv4, with optional CIDR) to which the isolated hosts are allowed to connect.
Blocklist
The Blocklist page allows you to manage applications that are restricted from running on your endpoints, preventing specified applications from being executed. The page displays a list of blocklisted applications, including their names, descriptions, and the time when each blocklist entry was last updated.
-
Blocklist Overview
-
This section provides an overview of all the blocklist entries. For example, you can view blocklist entries like Notepad Block - Test, which prevent specific applications from running on isolated systems, ensuring security is maintained.
-
- Blocklist Details Table
- The Blocklist Details Table provides detailed information about each entry, displaying the name of the application, description for additional context, and the time it was last updated. This table allows you to view and manage the entries, ensuring they align with your security policies. You can track the status of each entry and modify them as necessary to maintain proper access control and prevent unwanted applications from running.
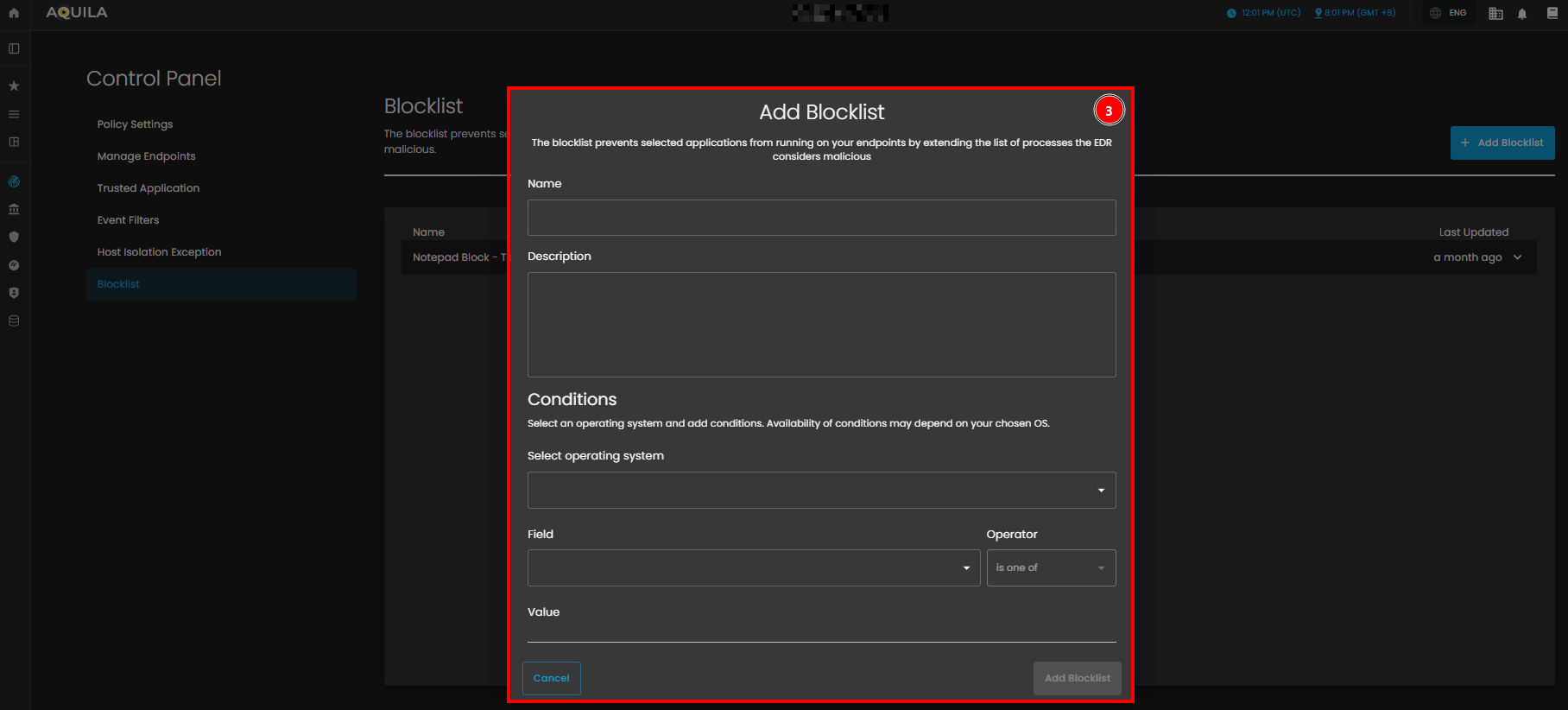
- Add Blocklist Entry
- When adding a new blocklist entry, a popup window appears allowing you to set up the entry. In this window, you can enter the Name of the entry and an optional Description. You can also define the Conditions by specifying the application and other criteria that should be blocked on your endpoints.
If you need further assistance, kindly contact our support at support@cytechint.com for prompt assistance and guidance.